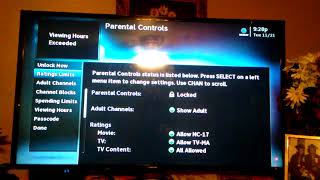
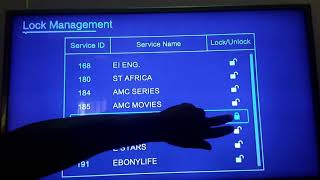
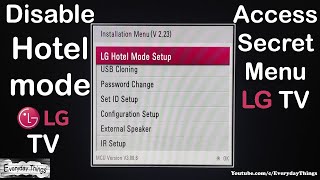
How to unlock a directv password
unlock
How Do I Crack Satellite and Cable Pay TV? (33c3)
Timecodes:
No transcript (subtitles) available for this video...
Related queries:
how to get directv password
how to get my directv password
how do i unlock a locked channel
how to unlock tv password